Cyber security has always been a key consideration for businesses – how do you protect your data and your documents? EMS in Microsoft 365 can help.
The good news is that keeping your organisation protected in the cloud is more manageable than ever. Microsoft say “Security can’t wait“ and offer a great set of security tools from right within Microsoft 365. This suite of tools is called Enterprise Mobility and Security (EMS). However, EMS is very different to the traditional approach to cybersecurity – and many businesses struggle with how to communicate the changes that EMS introduces to their employees.
In this article, I look at some of the common concerns and questions that end users have about EMS – and ways that you can address those concerns and communicate why you are doing things differently.
So, what is EMS in Microsoft 365 ?
EMS stands for Enterprise Mobility and Security. It offers great features like:
- Identity and Access Management – manages the identity of all your users/manages which devices can access your company data
- Information Protection – allows organisations to protect sensitive information using security policies that force users to apply classifications and protection labels to documents, data and emails
These features incorporate many different tools, but are fundamentally about defining who can enter your Microsoft 365 instance, and what they can do once they’ve logged in. As beneficial as EMS is, end users may have certain concerns about how it works. And this is why clear communication is so important.
Communicating About Identity and Access Management in EMS
Microsoft provides two specific tools for managing who can log onto your instance of Microsoft 365: Mobile Application Management (MAM) and Multi Factor Authentication (MFA). Both these tools have many benefits, but it’s important to communicate to people why you are deploying them.
Take MAM for instance. MAM controls access to specific corporate applications and their related data for all mobile devices and limits the sharing of that corporate data. Whether an organisation supplies corporate devices (laptops and phones) to its users or if it allows its workforce to use their own devices to access work-related applications, MAM will apply. This means that an organisation can remotely track, lock, encrypt and wipe their employees’ devices (albeit just the corporate applications and data).
While this functionality is great for cybersecurity, the fact that their employer can track their phone can sound pretty ‘Big Brother’-ish to employees. Users worry that their organisation can see their personal data if they are using their own device and not a corporate one. In reality, their company cannot see this data, but you need more evidence than this to assuage their concerns.
At FITTS we have developed a diagram which explains exactly what an organisation can and can’t see when MAM is installed on a user’s personal device. By communicating clearly, users are much happier to accept MAM.
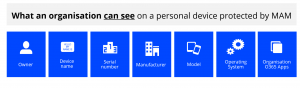
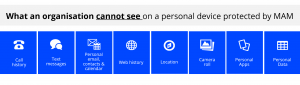
Another handy feature we’ve developed is a ‘MAM Matrix’ – this is a diagram that explains what a user has to do once MAM arrives on their device. This links to a ‘How to’ guide that takes the user through the steps of setting up MAM on their particular device (whatever the OS).
By communicating clearly about MAM, users find it less ‘scary’, and instead see it as a positive.
Communicating About Information Protection in EMS
Microsoft protects data in its cloud with Azure Information Protection (AIP). This protects corporate data by allowing more secure access to company resources and enables safe sharing of sensitive information internally and externally. Users must categorise, label and protect corporate information across Office 365 applications.
This can be a tougher ask for users – firstly the organisation must define its Information Classification Policy which specifies how it classifies information and set the minimum levels of protection that must be applied to each category of information. Examples of Classification:
- Internal
- Public
- Confidential
- Critical
Then users must apply sub labels to choose which added protection/encryption is needed – for example Internal Only or Recipient Only.
Now this is clearly far more involved than what many users are traditionally used to. It also forces them to make an additional decision whether they are composing a new email or creating a new document. That extra step can be frustrating and for many it will feel onerous. But, once again, communication is the solution.
For example, one question that comes up regularly relates to what classification and sub label to use for a particular scenario – so it’s vital that there is clarity around your organisation’s ICP (Information Classification Policy). You need to be able to provide clear advice that is easy to find.
Other common questions are:
- Can I send an email with a lower classification than that of a document that I attach?
- Is it possible to share a Confidential or Critical document/email when I am presenting in a Teams meeting?
- I need to send an email with an attachment to multiple users within an organisation – if I use the sub label Recipients Only, do I have to type in each recipient’s email address individually?
One way to communicate about AIP is to provide FAQs – covering the why, the how and the what for.
It can also be useful for users to see things from the point of view of a recipient of an AIP-protected email or document – especially recipients who are using Gmail or other email clients. We have often used step-by-step screen shots to show users what recipients can expect to see when they are in receipt of a protected corporate email/document and ultimately be equipped with answers to those potential questions posed by recipients.
Communication is key
Microsoft’s EMS tools give your organisation some incredibly powerful tools for protecting your instance of Microsoft 365. However, EMS does require your end users to change their behaviour – and to begin with at least, this may be perceived as onerous or invasive.
And this is why clear communication is so important. By helping users understand what’s happening, and using a variety of methods to explain why, they are much more likely to accept the change and incorporate it into their daily working habits.
Have concerns that your security isn’t up-to-scratch but not sure where to start? FITTS is offering a free security assessment funded by Microsoft to see where you’re falling short and with recommendations on quick wins and simple measures you could take, to ensure your people and your business are secure. Contact us today.
Jayne Sims
Jayne Sims is a Business Change Consultant at FITTS.
Jayne has worked in technology across different roles for 30 years both locally and internationally. Previously a Microsoft 365 technical consultant, Jayne now supports clients to adapt to their new technology changes through change management and adoption. More recently Jayne has worked in successful digital transformation projects effecting from 50 to 70,000 users globally – introducing cloud technology like Office 365 (Skype, Teams etc), Microsoft EMS, implementation of MRP/ERP solutions spanning Government, Aerospace, Manufacturing, Banking, and Global Technology companies.