In 2023, every organisation is keeping up with dynamic digital transformations as more data is generated than ever before. Security concerns are now higher than ever, as cyber threats continue to grow in volume and become more sophisticated. Security analysts are finding it harder to analyse, investigate, respond, and resolve the security alerts overload in a timely and effective manner. To stay ahead of these security threats, organisations are investing in advanced security technologies and implementing robust security strategy. Adopting a proactive approach of identifying threats by real-time analysis of event data, for early detection and prevention of targeted attacks, is the way to go. This is where Microsoft Sentinel Cloud-Native SIEM/SOAR comes in.
Microsoft Sentinel is a cloud-native next-generation Security Information and Event Management (SIEM) and Security orchestration, automation, and response (SOAR). As a SIEM it collects security data across multi-platform data sources and multi-cloud combining the usage of long-term storage, analysis, and log data with correlation of events, notification, real time monitoring and console views. As a SOAR it has a set of compatible software programs that will collect data on security threats from variety of sources and respond to those security incidents without the intervention of security analysts.
According to Gartner November 2022, SIEM Report Microsoft Sentinel is now recognised as a leader in the Magic Quadrant with its ability to deliver next-generation Security Operations in the cloud powered by AI and automation.
How can Microsoft Sentinel benefit your organisation?
As a cloud-native solution, the organisation is relieved of overhead infrastructure operations. When you do not have to worry about monitoring, maintaining, or scaling the infrastructure with every increasing amount of data, you are able to spend more time analysing and responding to threats. As an organisation you only pay for what you’ve used, based on the volume of data that has been ingested and analysed, and the data stored in Azure Monitor Log Analytics workspace.
At FITTS, we have first-hand experience from our customers on the benefits Microsoft Sentinel has offered them, significant ones being:
- Can be easily set up and deployed. As per Forrester’s Total Economic Impact report, Microsoft Sentinel is 48% cheaper and 67% faster to deploy compared to legacy SIEMs.
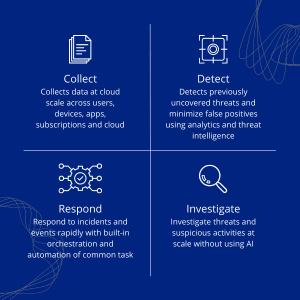
- Simplifies the collection of data from various sources in a single panel with optimised dashboards.
- Detect advanced threats and minimize false positives with AI-driven SIEM and XDR capabilities.
- Investigate prioritized threats with AI and hunt suspicious activities at scale.
- Efficient and effective response with built-in orchestration and automation of common tasks
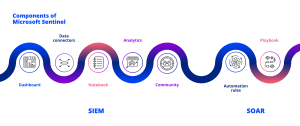
Key Components Dashboard
Microsoft Sentinel is packed with an in-built simple standalone dashboard that allows for data visualisation from the multiple connected sources in real-time.
Data Connectors
There are both built-in connectors from Microsoft Sentinel, and out-of-the-box to allow for data ingestion. Microsoft Sentinel can successfully ingest and correlate data from a broad set of log sources located on various cloud platforms (Azure, AWS, and Google Cloud), on-premises networking and computing infrastructure, third-party security tools (including firewalls), or Software-as-a-Service (SaaS) application.
Workbooks
Allow for monitoring of data by creation of interactive reports for gaining insights, Microsoft Sentinel not only comes with built-in workbook templates to choose from on the go, but also a versatility of creating custom workbooks across their data.
Hunting
Microsoft Sentinel features sophisticated hunting search and query tools based on the MITRE ATT&CK framework for proactive and manual investigations to uncover security vulnerabilities across your company’s data sources before an alert is raised.
Notebooks
Microsoft Sentinel supports Jupyter notebooks in Azure machine learning workspaces, which contain an in-built collection of frameworks and modules for machine learning, visualization, and data analysis.
Analytics
Microsoft Sentinel uses analytics to correlate alerts into incidents which reduces the noise by lowering the number of alerts to be investigated and reviewed.
Community
Powered by Microsoft’s Github, it is a powerful resource for threat detection and automation where new workbooks, playbooks, hunting queries, etc. are constantly added and can be used within Microsoft Sentinel.
Automation rules
Composed of triggers, conditions, and actions, they automate common security tasks and processes in Microsoft Sentinel. They can be triggered by events, incidents or alerts generated from the configured data sources.
Playbooks
Built on the foundation of Azure Logic Apps, Microsoft Sentinel’s automation and orchestration solution feature playbooks. They integrate with existing tools to automate your common tasks and simplify operations.
Deploying Microsoft Sentinel
As a cloud native SIEM/SOAR you don’t have to provision any service to spin Microsoft Sentinel up. With an active Azure subscription, Microsoft Sentinel can be enabled from Azure Portal by selecting the workspace you want to use or creating a new one.
Amplify your data estate security by staying ahead of security threats with Microsoft Sentinel Cloud-Native SIEM/SOAR.
Microsoft Sentinel is a cloud-native to go to a single pane of glass for threat detection, visibility, proactive hunting, and automated threat investigation and response.
Interested in an in-depth understanding of Microsoft Sentinel and its technical benefits to your organisation? We offer fully funded workshops on Defend against threats with SIEM plus XDR to get an in-depth deployment and understanding of Microsoft Sentinel Talk to us today to discuss how FITTS can uphold your security.
Clinton Isalambo
Clinton is a Cloud Engineer with a focus on security at FITTS. With experience spanning across education, hospitality, and ICT consultancy industry, he possesses a broad spectrum of knowledge on cloud infrastructure and IT security solutions.
He offers expertise around Cloud Security solutions including SIEM & SOAR, Identity and Access management, Information protection, Cloud app security and M365 security to help clients in enhancing their overall security posture and secure cloud environments.